Red Teaming?
#RedTeaming (2025-08-29) 
Heads-up, this might come up as a rant or even more so “why are you stating the obvious?”. Tbh i feel like i have to say it and take it off my chest smh.
The typical definition of a Red Teamer is someone who emulates/simulates an adversary. I will be using the words “hacker” and “Red Teamer” to refer a Red Teamer.
These days, there are so many “Red Teamers” who have earned the title by completing certificates from three-four letter’d companies. Most of them have not done a real Red Team operation but they yearn to become one. Nothing wrong in that, and I am not taking a dig at them either as certifications do have certain benefits.
The goal of this blog is not to criticize people who want to be Red Teamer by taking the certifications but to simply exhibit what is a Red Teamer and how can one truly become one. I’ll try to explain what I think is a non-negotiable skill to be a Red Teamer and hopefully try to explain how to operationalize.
Mindset First
First and foremost, Imho being a Red Teamer is a matter of Mindset. Red Teaming is all about mindset.
A true hacker does not learn Techniques, Tactics and Procedures by-heart. It is in his nature to break the rules just for the love of the game. That is how all these TTPs are discovered by the great people out there. One can master all the techniques and Tactics from MITRE, or any framework that the “industry” comes up with, by practicing, and still struggle to be a Red Teamer without having the right mindset.
Do not misunderstand. By no means I am advocating that learning the existing TTPs is not required or a waste of time.
“The big secret to breaking the rules is to make it look as if you are following them” - Johan Liebert
What is this “Mindset”?
Now what is this “Mindset” that I keep yapping about as if it’s some sort of esoteric wisdom? In fact, it is very simple.
The mindset of a hacker is to do not-so-right things in the right way.
A hacker’s mind at its core is operated on deception. That is what a true Red Teamer requires.
A true hacker is colourless, he can soak up anything and learn anything and is malleable. Learning to learn is a tool in their arsenal and I believe that is a skill that is a must to thrive to cosplay as a hacker. Red is just one flavour, true hackers can come in multiple and savour ‘em all.
Deception at the Core
One does not need to find crazy exploits to succeed as a Red Teamer but simply manipulate the flow by deception.
There are quite a number of incidents of social engineering where the attackers do not even use FUD RATS or fancy C2s. It is comical to know that even those crazy exploits are a product of deception.
For example, consider the following privilege escalation technique “KrbRelay”. The entire attack is based on deceiving the privileged process to unmarshal our COM object and resolve the OXID to our rogue server. Every step in the attack chain is literally the functionality and normal business, but somehow that leads to a universal privilege escalation.
- COM object marshaling Normal
- Moniker binding Normal
- OBJREF unmarshaling Normal
- OXID resolution Normal
- RPC authentication Normal
I am no exploit dev but I’d say at the core, every exploit can be reduced to one of two roots:
- deception (convincing a system or user to treat malicious input as legitimate)
- misconfiguration (where the system is already misaligned and grants unintended Write/Execute paths)
Whether it is a high-level social engineering ploy or a low-level memory corruption bug, the attacker is either exploiting trust or exploiting flawed assumptions in configuration.
Operationalizing the Mindset
As they say “It is not a bug but a feature”. Let me say it again, doing not-so-right things in the right way.
You wouldn’t wanna bang on the endpoints head on with the publicly signature’d tools or techniques, if the detection logics are built around technique . In this age with the state of the current defences, most of the fancy new tools or techniques will be flagged and will result in burning your operation if they are not weaponized surgically. Try to leverage legitimate features as much as possible.
Let us consider DLL hijack as an example, which happens to be one of my favorite techniques since it is “legitimate” . There are quite a number of DLL hijack variants . I want to use this as the main example since i feel it can be a one shot for all scenarios( stage 0/1, persistence and privilege escalation).
I am going to assume you are familiar with what a DLL hijack is and the different types of DLL hijacks. The variant I am going to use for the first case is DLL hijack within a vulnerable app inside user writable directories. It could be a stage 0 or even stage 1 depending on how you use. Consider the Python Hijack where you can make your benign dll execute when the python.exe is run from the folder,so if you pack the entire python exe and dll and ship it with the ruse of “obsolete software” ruse . Now there could be better ways you can deal with this but you get the gist.
The next case would be for privilege escalation and persistence together. Say, you discovered your low-priv user can write to a system folder eg ., system32. Now you have the potential to escalate your privileges with the very same DLL hijack vector.
We will use the wptsExtensions.dll for this one. Now once you create your own Wptsextensions.dll and place it inside the vulnerable directory, you can run the code with system privileges. But since this requires the system to restart it will not only run your code with system privileges but also run it whenever the system is restarted.
To each [operator] their own, maybe try to create a new account with a similar naming to that of a guest account on the local machine. This way your newly created account stays local and is not tied to any domain groups and yet you can access system resources. Or if you prefer to get a beacon straight off , you might simply have your DLL do that. Thought I would stress again, known malicious behaviours like shellcode injections straight off the github will kill it all. Try to implement atleast the bare minimum to knock off the telemetry
Case 1:
Now lets get back to a bit high level and look at the case of the Uber hack from 2022, the attacker did not pull any crazy zero days or exploits but simply deceived for initial access and abused the existing functionalities. The attacker literally accessed all the resources as the user he just compromised , everything legitimate and normal. No games with LSASS or any tokens that might tick off the defenses, just oozing off the red aura with that PAM access.
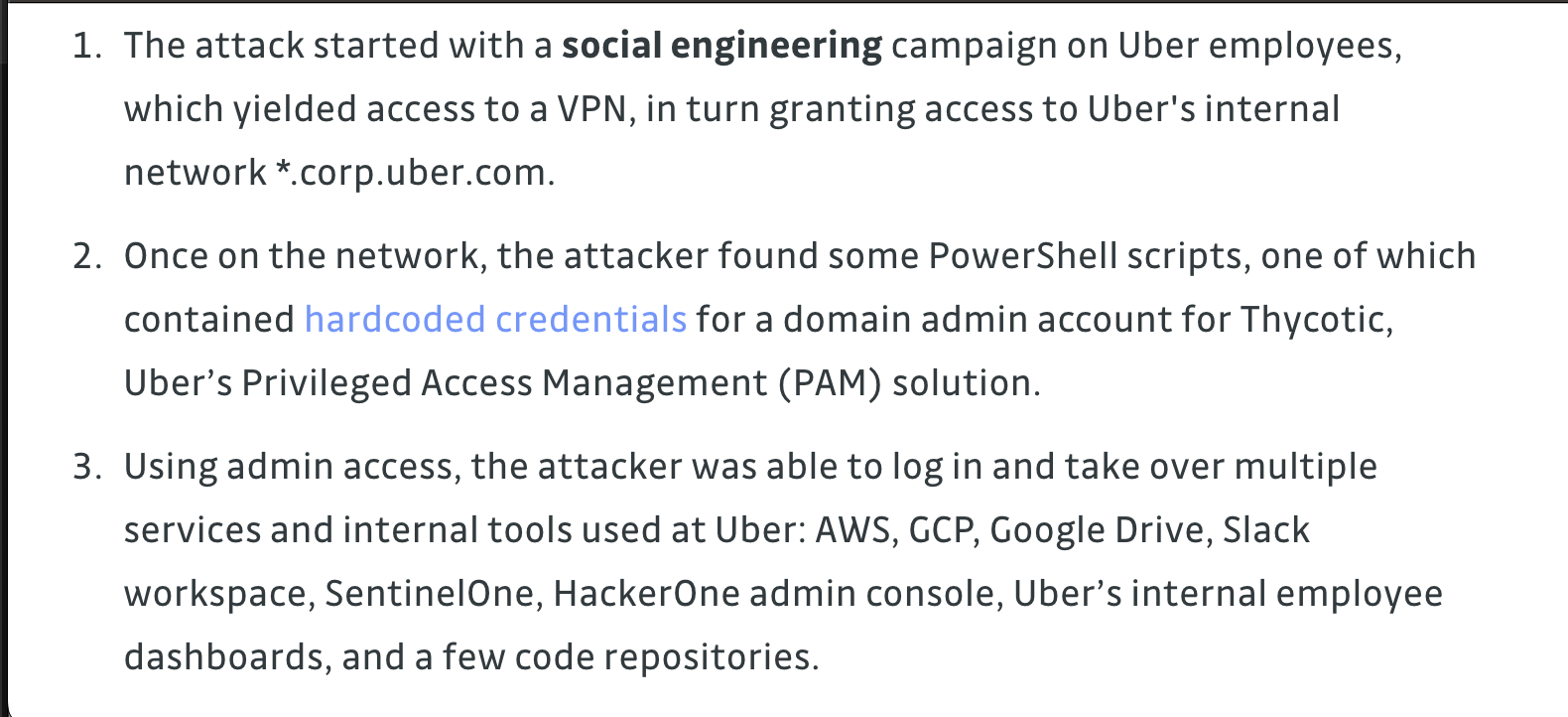 Although one
could argue that the attacker was really lucky, I’d say that it was a
gamble, as all the social engineering campaigns, with really good odds
when you consider that the attacker might have done due diligence in
doing OSINT and pinned down exactly who he wanted to target.
Although one
could argue that the attacker was really lucky, I’d say that it was a
gamble, as all the social engineering campaigns, with really good odds
when you consider that the attacker might have done due diligence in
doing OSINT and pinned down exactly who he wanted to target.
Case 2 :
Let’s take another case. I might be oversimplifying things here without getting into the technical specifics but I hope you get the gist. You are tasked with creating a phishing campaign. You follow your knowledge base and use the techniques that course you recently took has taught you. But you discover “whatever” you learnt has become obsolete and your mails are being pulled and being marked as spam, or even worse, being deleted automatically.What do you do now?
At the same time, your bud who works in the marketing department is successful in landing in the client mailboxes to sell his snake oil. He hasn’t taken any training to create phishing campaigns, he does not use gophish to send his mails, he does not use any fancy techniques to bypass email gateways. For all you know, he might be using Mailchimp/MailerLite, or some other Email service, and has a generic marketing template and somehow his mail lands in the mailboxes of the clients.
Why? Are those email services better than what you use? Do a google search and you will end up with the following.
Marketing emails are not marked as spam because:
- they often come from legitimate sources who have obtained consent
- maintain good sender reputations
- use proper email authentication
- provide clear unsubscribe options
- send relevant content to engaged recipients
So to send a good phishing campaign, try not to send phishing mails but try to send legitimate “marketing” mails with some nuances. You simply wear the cloak of a digital marketer for this task. Remember a true hacker is colourless, he wears many cloaks. Whenever I go to any conferences, I’d register by typo squatting my first name (John doe becomes jhon doe) and then setup an outlook rule that matches “jhon” ,so that any mails i receive from the marketing teams are safe and secure and i can reuse their templates.
Conclusion
I’d stress again that deception is another skill a Red Teamer must have to cosplay a hacker. Deception does not invalidate the technical skillset(i’d still need to know the command and the tool to perform lateral movement) rather it exponentially increases the authenticity. It goes hand-in-hand. Hopefully I have convinced you that deception is a supreme add-on to have in your kit.
